Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
Black Hat USA is one of the top cybersecurity conferences in the world. It gives vendors and customers an opportunity to learn from some of the top researchers, see what new products are available, and network with our peers. It’s an exciting and valuable experience but can also be overwhelming. With a Business Hall, Keynote Speakers, and Technical Briefing sessions to choose from, it’s easy to leave wishing you had more time. Here are some tips to get the most out of the event.
No other events conflict with the Keynote presentations, so there are no excuses for missing these. We are particularly excited about hearing Kemba Walden talk about the National Cybersecurity Strategy Implementation Plan and the National Cyber Workforce and Education Strategy. If you’ve not read through the document, one of the key lines reinforces the importance of this initiative:
“Cybersecurity is essential to the basic functioning of our economy, the operation of our critical infrastructure, the strength of our democracy and democratic institutions, the privacy of our data and communications, and our national defense.”
Now that the strategy has been outlined, it's time to get to work implementing, learning, and modifying it for the evolving threat landscape. Kemba’s talk should give us clarity on what to do next.
The Briefing Review Board for Black Hat always has its work cut out for them. They need to evaluate thousands of proposals to select about 100 that will educate and hold the interest of the security professionals who attend each year. They also need to balance topics across 22 tracks and predict what trends are just a brief flash and what trends will be part of the cybersecurity future. Check out the briefings list in advance and fill in your schedule accordingly. Remember, there are nine or ten briefings running concurrently in each of the five sessions Wednesday and Thursday.
Track # Briefings AI, ML, & Data Science 15 Exploit Development 14 Application Security: Offense 13 Enterprise Security 13 Hardware / Embedded 12 Application Security: Defense 11 Cloud Security 11 Data Forensics
& Incident Response 11 Network Security 10 Platform Security 10
Looking at the top tracks provides us with a view of what the Briefing Review Board believes are top of mind with the security community. AI and ML top the charts, followed by more traditional interests like exploit development, application security, and enterprise security. Understanding what’s hot on the minds of the Black Hat Review Board is interesting, but it also must be relevant to the needs of the business. A lot can be learned from which sessions are better attended than others.
Don’t miss our Chief Security Officer, Chris Denbigh-White, when he presents on Wednesday at 5:20 PM in Mandalay Bay L. Chris’s presentation is titled Insider Risk Management and DLP - Double Down and Beat the House. He will talk about the convergence of Data Loss Prevention (DLP) and Insider Risk Management (IRM), and how that benefits security teams. DLP traditionally focuses on reactive policies to protect data while IRM looks proactively at user behaviors. Each can give security teams information, but together they can give a rich view into the who, how, when, where, and why.
It should be no surprise that “Artificial Intelligence, Machine Learning, & Data Science” is a hot track this year with 15 briefings over the two days plus Wednesday morning’s Keynote. That’s three times as many briefings on the topic as last year.
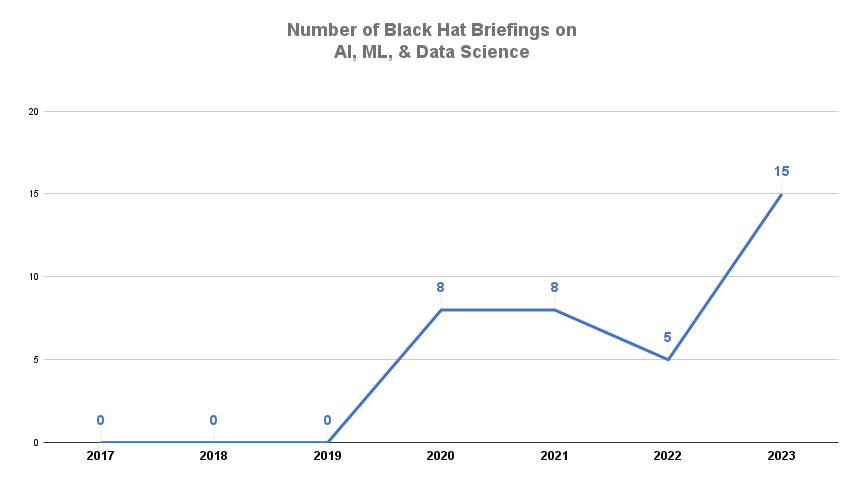 |
AI and ML have generated a lot of buzz this year. We have talked about the confusion over what ML can and cannot do. As organizations adopt technologies like ChatGPT, they need to understand how these platforms can result in data loss. It’s also useful to understand how these technologies can help improve your defenses. For example, the Reveal platform from Next leverages ML on each endpoint to classify data as it is created and used, to establish a risk profile for each user, and to autonomously analyze behavior on and off the corporate network. We’re the only DLP and IRM solution that does this to make your data protection program more effective.
Micro Summits offer an opportunity to focus on a topic with broad applicability to security practitioners. We think the cyber insurance track is worth consideration.
Insurance providers have seen their payouts soar as damages rise from breaches and ransomware attacks. Some firms have stopped providing coverage for attacks by nation-states and all are requiring more stringent controls. Understanding what your organization can do to improve your defenses and lower premiums is time well spent.
Black Hat attracts a lot of vendors and provides a good opportunity to compare capabilities. Make a short list of vendors you want to investigate and prepare a short list of questions about your use case(s). Be prepared to drill down on the capabilities that are important to your organization, including ease of use, time to value, and operating overhead. Make sure you consider your technical environment and internal capabilities. Lots of legacy solutions were designed for a time when all applications ran locally. Adapting them for a cloud-first environment can require a lot of extra work.
For some other perspectives on how best to prepare, here’s a video we created during the RSA 2023 event asking what’s the one piece of advice for a 1st timer, or a 1st timer since COVID.
Check Out Next Reveal
Reveal takes a different approach to data loss protection and insider threats than the legacy solutions. Reveal is a cloud-native platform built for today’s work environment. We moved machine learning to the endpoint for protection on and off the corporate network. Rather than requiring teams to pre-classify all the data in the enterprise before protection can begin, Reveal inspects and classifies data in real time as data is created and used.
Reveal protects sensitive data and user privacy. Unlike legacy DLP and employee monitoring solutions, we started with a “secure by design” approach to building Reveal. We use pseudonymization to detect and mitigate threats without compromising the privacy of users and prevent bias in monitoring users’ activities.
You can find us at booth #2408 this year when we’re not delivering Insider Risk Management and DLP - Double Down and Beat the House. We have a lot of new things to show. Listen to one of our theater presentations, meet with our experts, get a demo, and grab some giveaways when you stop by.
Do you have a specific DLP or IRM challenge you want to discuss with us? Book a meeting and we’ll see how we can help you improve your data protection program.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources

